TOTAL SECURITY CENTER
An ecosystem of security-related services backed up by a resilient and reliable infrastructure.
Our expertise in the areas of Infrastructure & Networking Management and related services.
Our services are provided H24
Among the services we offer are:
Our expert services are divided into:

SOC - Security Operation Center
Today, the SOC solution proposed by SK3 is a point of reference for its customers; an interface to an all-encompassing security environment; not just a service centre, but more importantly a centre of expertise that is always up-to-date, on high alert, and in constant contact with national and international entities that play a role in security, alerts and developing an automatic alert process for company managers (Security/DPO, etc.)

NOC - Network Operation Center
The objective of NOC is to prevent inefficiencies and latencies for the end user, who through monitoring, patching and infrastructure management systems, must perceive the least possible impact of an incident/alert.

SPOC - Single Point Of Contact
Created with the aim of providing a single point of contact to receive, track and manage all support requests from S3K customers.

Infrastructure Management
We provide IT infrastructure, network, and physical and logical security management support to our customers.

Application Management
Ranging from the idea conception phase – carried out together with the customer in design thinking sessions – to the domain analysis and definition of “use cases”, flows and processes by means of advanced modelling languages.

Managed Services
Dedicated help desk services and specialised on-customer-premise support. S3K's tailor-made solution focuses on the customer’s needs to offer system services at all levels.
The S3K Total Security Center:
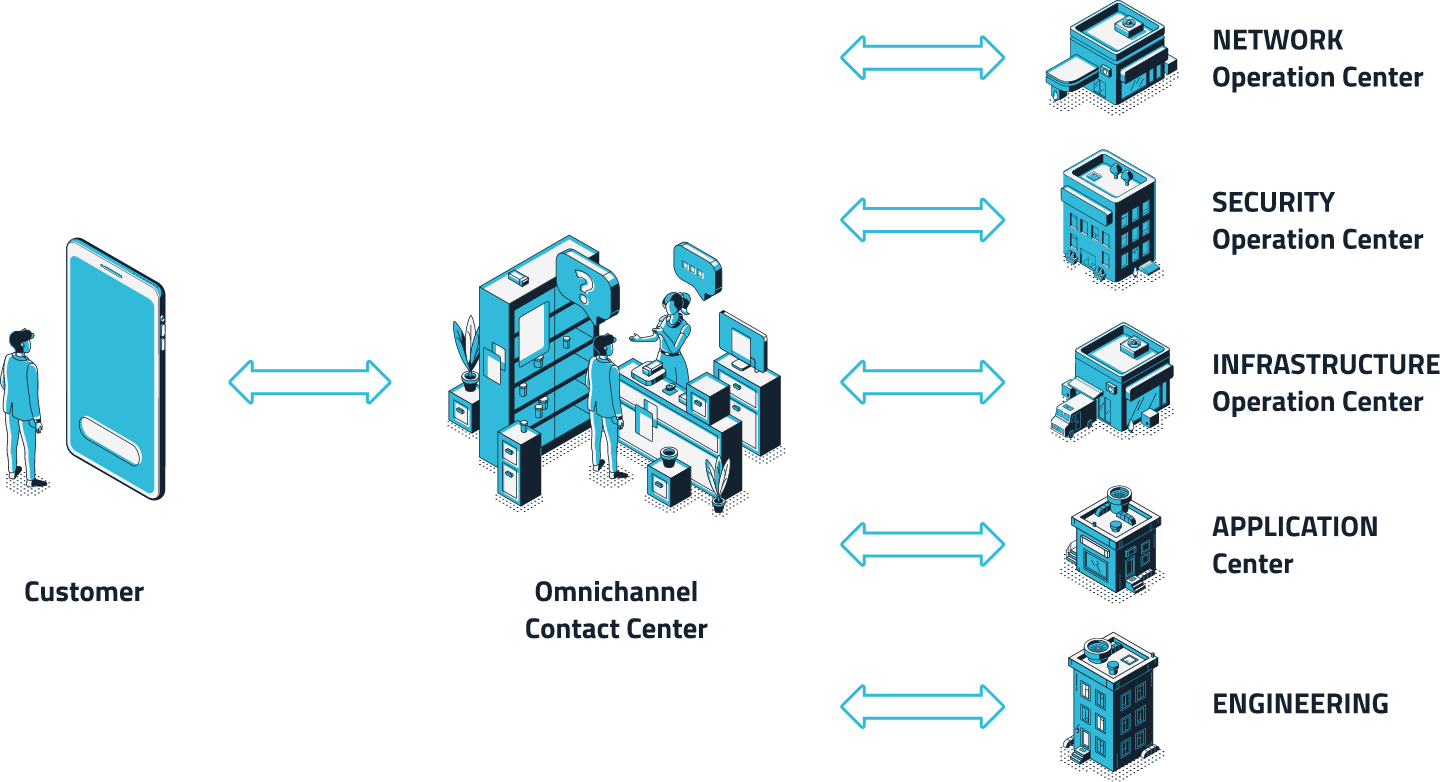

Total Security Center services include those of the Network Operation Center, which are comprised of Provisioning, Monitoring, Troubleshooting, Reporting and Management services.
