CYBER SECURITY
Developing digital security with technology implementations that are inherently secure and resilient.
The S3K specialist Cybersecurity Team possesses the technological expertise and
IT security services that allow it to cover the market areas of Government(PAC E PAL), Digital services provider, Energy, Utility , Oil & Gas, Finance, HealtH & Life Science, Industrial Manufacturing, Consumer Goods & Automotive, Telco & Media:
- Risk Assessment & Management • Business Continuity & Resilience
- Cyber Defence
- Digital Identity management & Privileges
- Application Security (API, ERP, secure code review)
- Data Protection
Among the services we offer are:
Our expert services are divided into:

AntiSpam/ AntiPhishing
AntiSpam service provides full protection of the Client’s mailbox against messages defined as “spam”, according to options provided by the standards. In particular, all messages that contain or are suspected of containing Phishing in the subject line and/or body are blocked and reported.

Vulnerability Assessment & Penetration Testing
The Vulnerability Assessment Service is by definition the process of defining, quantifying and categorizing all possible vulnerabilities in a Client’s infrastructure (HW, SW and application). The Penetration Test Service verifies the robustness of the infrastructure under review by simulating attacks on the Client’s perimeter and exposed elements. The Vulnerability Assessment and Penetration Test are practical tools that help to pinpoint weaknesses and introduce the necessary protection measures (Remediation).

Malware Analysis
This is the study of malicious code with the aim of understanding its content, purpose and, possibly, origin. These activities can be provided together with S3K’s SOC in automated or manual mode. In a manual analysis process, more details regarding the malware and its purpose can be highlighted. The moment a ransomware attack is detected by endpoint protection tools, a process is triggered to better understand possible exposure to the attack, gathering the necessary information from the environment and managing the necessary investigative steps.

End point protection
in S3K we offer a service, on-premise and not, for the complete protection of endpoints through the definition and application of appropriate security policies, event monitoring and incident management. An immediately available team of security experts ensures immediate detection of malicious indicators and Treath Intelligence.

Additional services supported by technology solutions:
- Automated penetration testing
- Cyber security Asset management
- Enterprise secure access and secure remote support
- XDR platform & MDR & NDR
- Data protection & data loss prevention
- Identity access management & priviledge access management
- Secure Authentication
- SOAR (security orchestration automation and response)
- SIEM (security information and event management)
- Security policy management & vulnerability management
- Vulnerability assessment and management
- Network Security Detection & Prevention
- Cyber Deception
- File based attack prevention

Security Awareness
A training path with a complete Cyber Security Awareness program for the entire workforce, based on cognitive and inductive methodology, in order to increase the employee awareness of the risks of the digital sphere.

Secure Web Gateway
We realize complete and integrated solutions for the protection from unauthorized traffic, for the control of incoming and outgoing data while users web browsing, with functions of blocking traffic from malicious websites, viruses and malware that can cause attacks on the network and data. The Web Gateway allows users to access only approved and secure websites.
The S3K Team provides support for security posture self-assessment, identifying measures that can bring growth in the cybersecurity maturity model.
Best Practices are constantly updated in response to ever changing market needs, with the monitoring of the threat scenario (Threat Intelligence, Deep & Dark web monitoring), understanding and predicting of attackers’ interests (Attack Trends), and, consequently, introduction and steering of updated risk assessment processes. They also require the introduction of protective measures for existing assets and for new technology areas gradually being adopted by most Organizations: Cloud Computing, IoT networks, AI tools, Edge and Fog computing, industry 4.0.
Our approach to addressing cybersecurity challenges that crop up in the 5 layers of the attack surface:
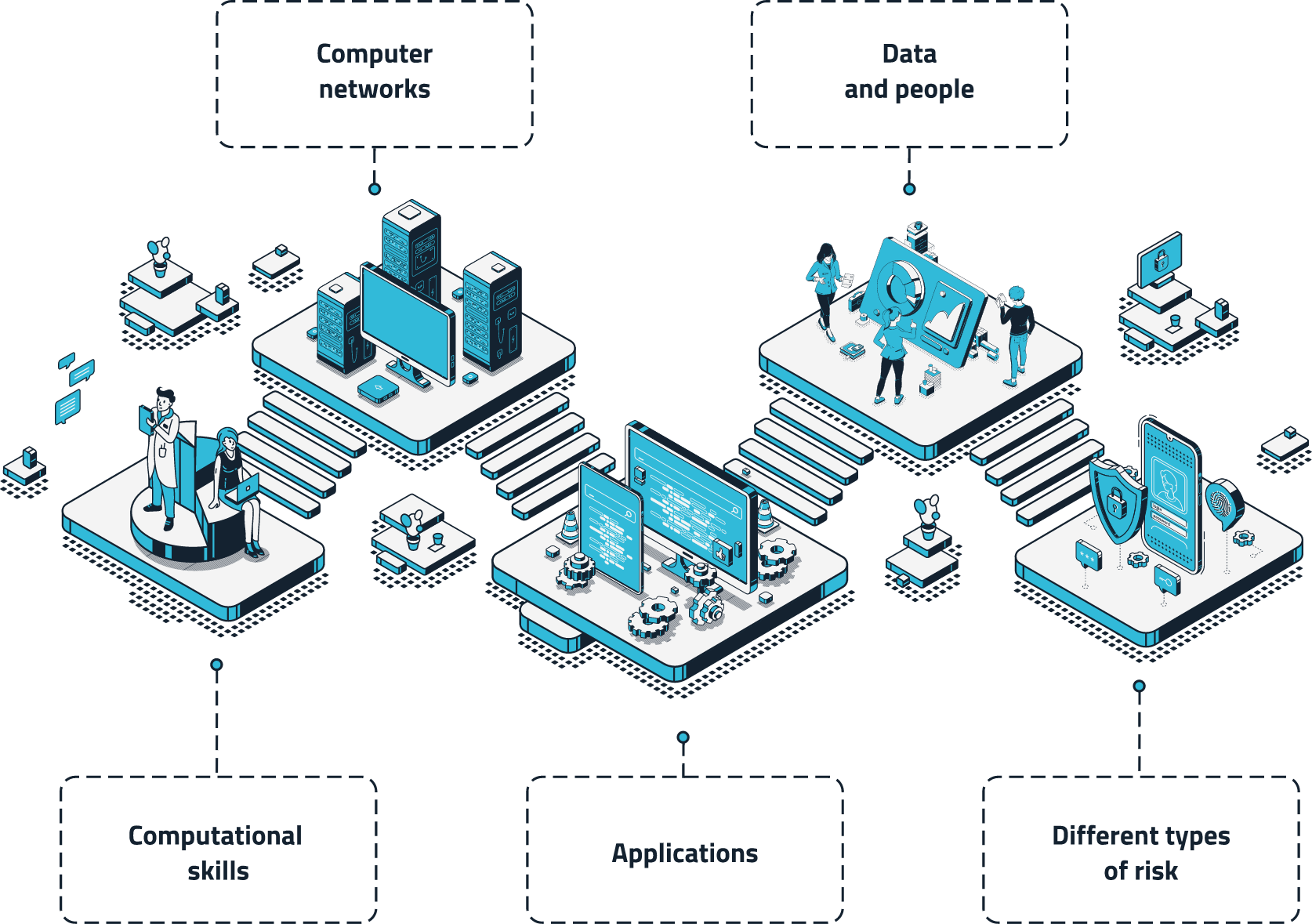

We support and govern Security Transformation processes, applying a Total Security approach to each project, based on a consolidated Security Value Chain methodology. The Team’s approach is in line with the National Cybersecurity Framework, bringing its own vision to each of the 5 steps: Identify, Protect, Detect, Respond, Recover.
