SOC
A DECISION-MAKING SUPPORT PROVIDER WITH
A SECURITY ENVIRONMENT INTERFACE.
A SOC is a facility that monitors the security status of IT of a company or more companies in the case that the SOC.
Within the SOC, people and technologies and processes have the task of keeping under control what happens in data traffic, to prevent incidents due to attacks that target IT resources and staff, whether they are in the company or on the move.
For medium and small companies the use of SOC is recommended as a service included among the managed security services of an external provider.
The increase in the attack surface due to smart working, the cloud, hyperconnectivity and new work tools have generated a significant increase in risk exposure which needs to be managed by prevention rather than by an after-care approach.
What services do we offer?
Our expert services are divided into:

Security Awareness
giving prominence to training personnel on security issues so they can deal with them effectively.

Threat Intelligence
This covers the three areas of IT, namely:
- Cyber Threat Intelligence (CTI) , which is evidence-based knowledge;
- Tactical CTI, entailing the use of technical information and IOC to identify the threat.
- Operational CTI, seeking to describe the motivations and capabilities of attackers.

Monitoring and Anomaly Detection
This service detects events with behavior that deviates from the “norm”, using specific computational algorithms to highlight significant and appreciable deviations from the norm.

VA/PT
Security checks carried out periodically on the Client’s infrastructure by means of an “appliance” provided by S3K and connected to the LAN. Our virtual Team of ethical hackers undertakes black or white box security audits according to the agreements and NDAs signed with the client.

Incident Handling
This service addresses Cyber Security incidents in the ICT environment with potential impacts requiring specialist analysis skills.

Digital Forensic
Technical and Legal support in the Cyber Security field for the analysis and forensic management of Security events.

End Point Security & Priviledge Management
Management of security of enterprise endpoint/server equipment. The Privilege Management service is geared towards managing external access of privileged accounts to business-critical servers/systems.

Forensic Analysis
to fully understand threats before they become security events.

Early Warning
This service provides an early warning of a possible vulnerability in the system before it is detected by Vulnerability Assessment (VA).

Security by design; the design of new digital experiences and systems by risk-assessment and the integration of security features from the outset should become a foundational paradigm of a business, just as much as a culture of security should be instilled in the company itself, ranging from staff to suppliers to external contractors.
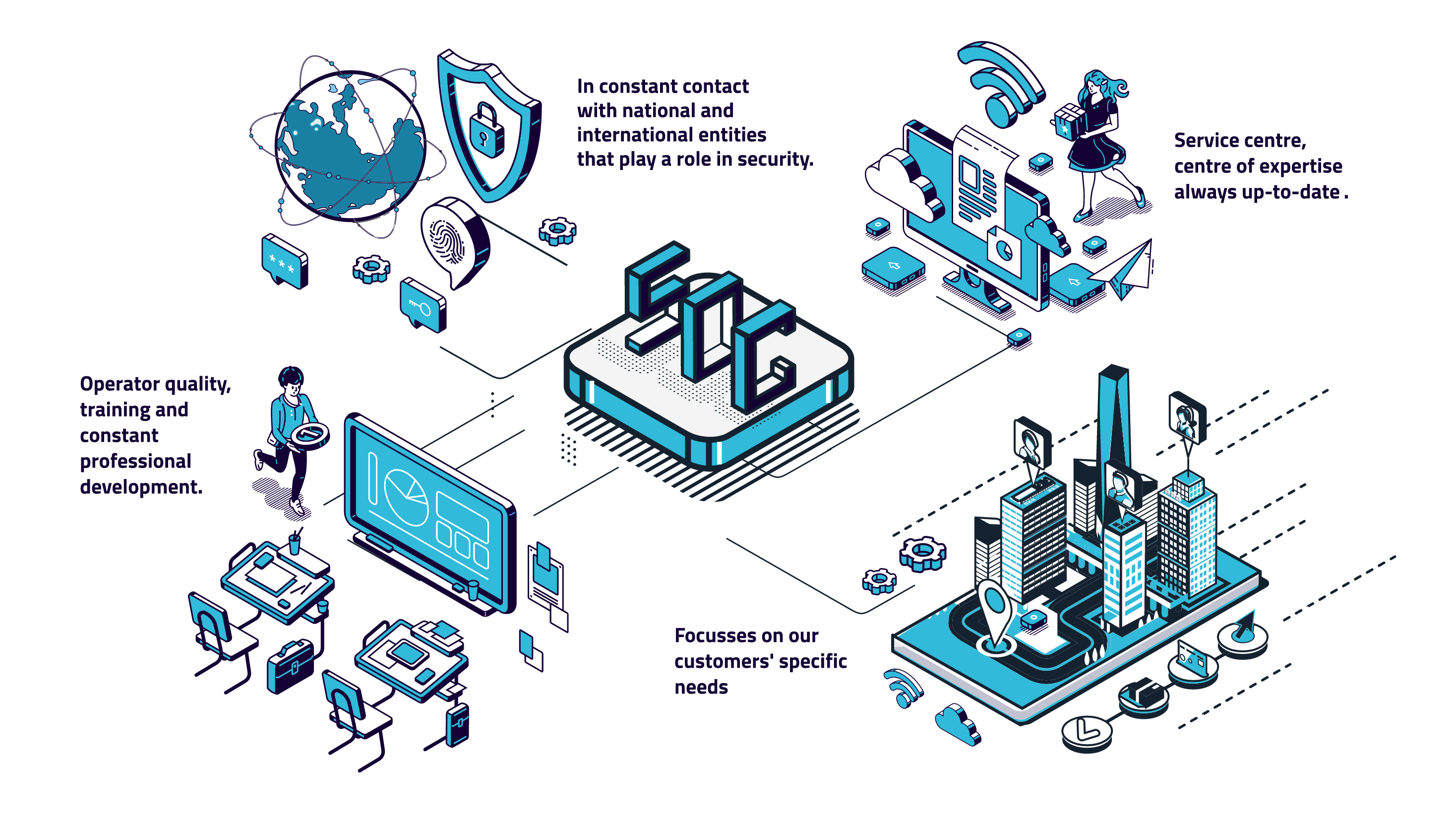
What makes our company unique?
Today, the SOC solution proposed by SK3 is a point of reference for its customers;
It is an interface to an all-encompassing security environment; not just a service centre, but more importantly a centre of expertise that is always up-to-date, on high alert, and in constant contact with national and international entities that play a role in security.
This is the focal point: in fact, risks in the banking world may vary to those in the world of health professionals.
